Data at the Sunny Beach
Many people have already planned their Spring vacation. Have you?
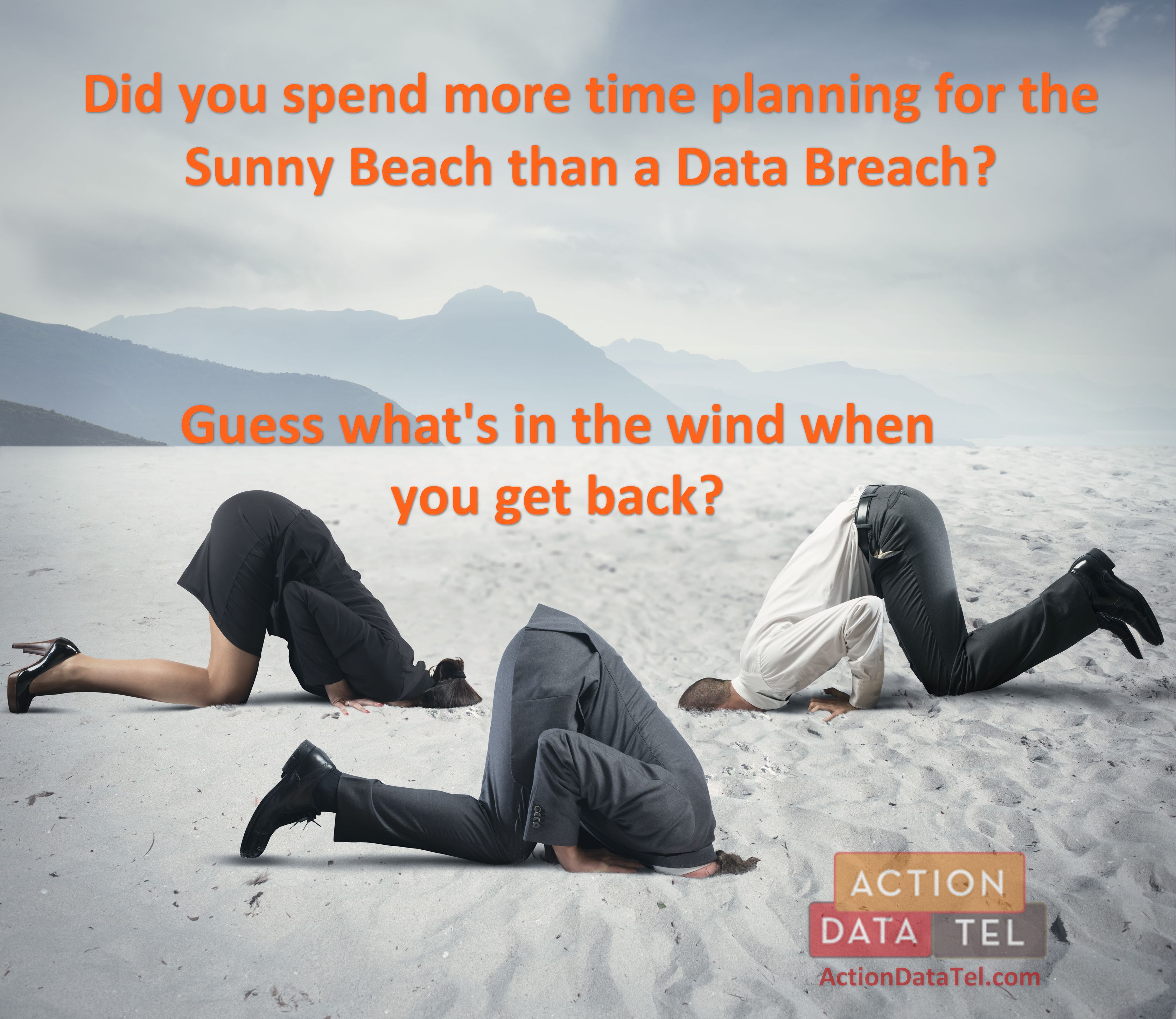
I’ll bet that you have spent more time thinking and planning for your next vacation than for the protection of the most vital asset in your business – your client’s or patient’s confidential information.
Don’t think a possible data breach is worth a second thought? Think again.
Imagine yourself on the white sandy beach sipping an umbrella drink, when your office manager calls, “I really hate to bother you, BUT…The bank just called. There are suspicious transactions…Three clients have called in this morning saying their bank is reporting fraudulent activity on their accounts…I think something is really wrong here.”
POOF! The anticipation of relaxation and a stress-free week in the sand is replaced with a high-dollar one-way ticket home and months of governmental questioning.
 “Your IT guy has it handled,” you say? Does he? Have you EVER REALLY checked?
“Your IT guy has it handled,” you say? Does he? Have you EVER REALLY checked?
Here are Five questions to ask your IT Service Provider. If these questions are not answered correctly, they are not working to protect you. The HHS HIPAA breach investigators are going to find big problems when your data security breach is investigated.
-
Are all systems up to date and patched automatically? (should be yes)
-
Are the firewall logs routinely and automatically monitored? (should be yes)
-
Do you test our data backups weekly by validating data restores? (should be yes)
-
Have we implemented Sandboxing or Application Whitelisting? (both should be yes)
-
Have all our computers been upgraded to Windows 7 or higher? (should be yes)
If your IT Service Provider inadequately answers any of these questions, you should stop planning your vacation NOW, and start looking for another IT Service Provider.
The fact is, most business owners don’t know the answers to these questions. Additionally, most businesses are not as secure as they should be. In most cases, the current IT Computer vendor fails to properly secure the computer systems, or just fails to monitor and act on suspicious activity. But it’s your responsibility as the business owner or manager to ask the probing questions.
Here is an excerpt & link to a recent HHS enforcement page for your reference.
NOTE: We include the reference to recent enforcement action for illustrative purposes. It is not intended to create an atmosphere of fear, but rather to illuminate that HHS IS serious and they actually DO take action when there is a data breach.
– December 2014 –
Anchorage Community Mental Health Services (ACMHS) has agreed to settle potential violations of the Health Insurance Portability and Accountability Act of 1996 (HIPAA) Security Rule with the Department of Health and Human Services (HHS), Office for Civil Rights (OCR). ACMHS will pay $150,000 and adopt a corrective action plan to correct deficiencies in its HIPAA compliance program. ACMHS is a five -facility, nonprofit organization providing behavioral health care services to children, adults, and families in Anchorage, Alaska.
OCR opened an investigation after receiving notification from ACMHS regarding a breach of unsecured electronic protected health information (ePHI) affecting 2,743 individuals due to malware compromising the security of its information technology resources. OCR’s investigation revealed that ACMHS had adopted sample Security Rule policies and procedures in 2005, but these were not followed. Moreover, the security incident was the direct result of ACMHS failing to identify and address basic risks, such as not regularly updating their IT resources with available patches and running outdated, unsupported software. 
Here is the link to the rest of the publically-visible settlement bulletin.
http://www.hhs.gov/ocr/privacy/hipaa/enforcement/examples/acmhs/acmhsbulletin.pdf
Can you believe it? $150,000 (and who knows how much in attorney’s fees) because they didn’t update their software? And malware – that’s a virus, right? Why on earth wouldn’t they have installed a good anti-virus program?
Even if they DID have anti-virus software installed, it alone is no longer an effective means of controlling MalWare (viruses, trojans, worms, and more). You must also employ other best practice techniques to layer computer security. It’s not rocket science, but it’s not obvious either!
“97% of all Data Security Breaches are avoidable by implementing LOW COST basic or intermediate controls.”
A modern IT company will have an automated system which will keep all your computers fully updated and patched. They will be able to monitor your machines to KNOW if you were a potential target of a malware attack, and REPORT this to you. This is not an all inclusive list of the advantages of monitoring, but you get the picture.
For help confirming the answers to these five simple questions about your business, pick up the phone and dial. We are happy to help. After all, no one should have an expensive, anticipated, and well-deserved vacation cut short for such a simple reason.
Call Action DataTel today to schedule a Comprehensive Computer Networks Security Review.